This page applies to those VPNs that use PPP – that is, PPTP and L2TP. The security settings (authentication and encryption) are irrelevant with L2TP, which uses IPsec for security. So for L2TP only the ‘IP address assignment’ section is relevant.
If you are using PPTP, then these settings could be tweaked to give the best security – it is possible that if left at defaults, Windows connects without encryption, as indicated by the black text in the Draytek ‘VPN Connection Status’:
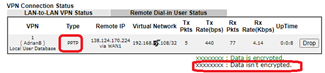
–
PPP Settings
Screenshots below showing where PPP is configured. Left: Draytek, right: Windows
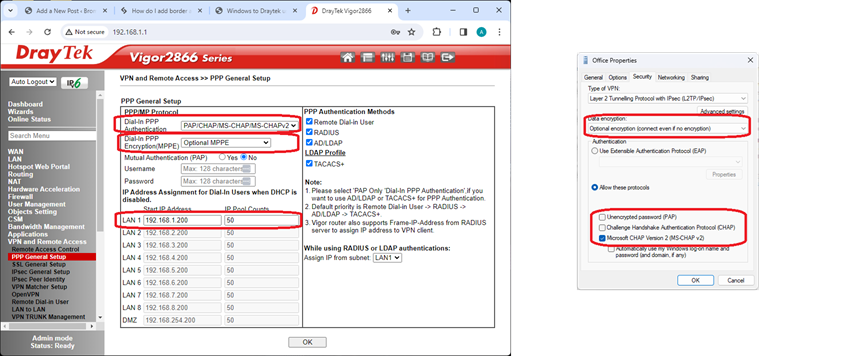
PPP is used by PPTP and L2TP VPN connections to authenticate usernames, encrypt data and assign IP addresses.
Several different authentication and encryption algorithms are supported. Each end of the VPN connection (Draytek and Windows) have one or more of these algorithms enabled, and negotiate which to use as they connect. Given several choices, the connection should try to negotiate the strongest. If a common set of algorithms cannot be found, the connection will fail. Remember that this only matters if you are using PPTP, as with L2TP security is taken care of by IPsec.
–
Authentication protocols, from weakest to strongest are:
- PAP – CHAP – MSCHAP – MSCHAPv2 – EAP
PAP, CHAP and MS-CHAP are now considered too insecure (PAP transmits passwords in plain text!). Draytek support all except EAP, and by default all are enabled. Windows supports all and by default MS-CHAPv2 is enabled. (Depending on how the VPN was created – using the GUI or PowerShell – MS-CHAP may also be enabled). VPN connections should therefore work out-the-box, and should use the best common algorithm available – MS-CHAPv2.
On the Draytek, the ‘Dial-in PPP authentication’ box controls the algorithms used. You could, if you are wish, disable the weaker algorithms. Depending on the router model, you can choose option ‘MS-CHAPv2 only’ or ‘CHAP/MS-CHAP/MS-CHAPv2’ in the drop-down box.
On Windows, the properties of the VPN network show the authentication properties, accessed by running ‘ncpa.cpl’.
–
Encryption is optional but if used will be MPPE (which is a Microsoft algorithm). MPPE comes in different strengths, so encryption options from weakest to strongest are:
- None – 40bit – 56bit – 128bit
The strength only matters to PPTP connections. L2TP connections use IPsec for encryption, so additional PPP encryption is irrelevant (I’m not sure that PPP encryption is even used with L2TP, but have no way of determining this. I think its unlikely, as encryption-within-encryption, will will only make things slower and packets larger).
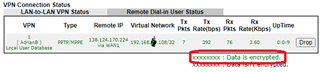
At the Draytek, the Dial-in PPP encryption can be left at the default ‘Optional MPPE’ for L2TP, but could be changed to ‘Maximum (128 bit)’ for PPTP. Connections should now be encrypted:
IP address allocation. This section applies to PPTP and L2TP connections.
When the user connects, they will need an IP address from the LAN they are dialling into. Draytek have several ways of dealing with this:
- If DHCP is enabled on the router LAN, PPP will use that to assign an IP
- If DHCP is not enabled on the LAN, PPP will assign an IP from its own ‘pool’ of addresses
- The user can be assigned a fixed IP address
No 1 is the easiest, and is the default. No 2 is also enabled by default, and will kick in if you disable DHCP on the LAN. No 3 is a property of the user’s VPN profile, and can be used without disabling 1 or 2.
There is more to IP allocation than just an IP address – there are options such subnet mask, default gateway and DNS servers to be set. These are not configurable in PPP, instead PPP uses settings from elsewhere to allocate these options.
- Subnet mask is always 255.255.255.255
- DNS server IPs are inherited from those set on the LAN DHCP server. If DHCP is disabled on the LAN, then PPP does not provide DNS servers. They will have to be manually added in the Windows VPN connection properties.
- Default gateway is a discussion for another day.
That concludes the discussion around Draytek PPP settings. To summarise:
- PPP is only used by PPTP and L2TP VPNs
- PPP security is irrelevant for L2TP
- IP allocation can be automatic, or by setting a fixed IP for the user
- Both the Draytek and Windows have the correct default settings to just work out-the-box.