When a Windows IPsec-based VPN (eg L2TP or IKEv2) connects to the Draytek, a whole load of negotiations take place to ensure the data is secured. We will not go into great detail about IPsec here, but will give a quick overview and describe how this relates to Windows/Draytek connections.
The IPsec negotiations determine, amongst other things, which IPsec security algorithms will be used. IPsec requires a particular combination of encryption, hashing and DH Group algorithms (together known as a ‘proposal’) to connect. Each of the algorithms has several different versions, each with different levels of security. From least to most secure these are:
- Encryption: DES – 3DES – AES128 – AES256 (DES and 3DES now considered insecure)
- Hashing: MD5 – SHA1 – SHA256 (MD5 considered insecure)
- DH group: G1 – G2 – G5 – G14 – G15 – G19 – G20 – G21 (G1 and G2 now considered insecure)
A proposal will contain one each of these elements, for example AES128/SHA1/G5 or AES256/SHA256/G21.
| Note: it is possible to configure IPsec without encryption, just hashing. This is known as ‘AH’ (Authenticated Header) but is rarely (if ever) used, and will not be discussed here. |
Several pre-configured proposals are enabled on both the Draytek and Windows. For a connection to succeed, the two ends must have a common proposal (this is why IPsec can be tricky to get right). When you connect, the two ends negotiate which proposal to use. Windows sends its proposals to the Draytek; Draytek does the same to Windows and the two devices negotiate a common proposal. If they cannot, the connection fails.
Out-of-box, Windows and Draytek have several common proposals, the VPN will connect, and you could stop there. But you may wish to increase the security to ensure the older, less secure algorithms are not used. DES, 3DES, MD5, G1 and G2 should be disabled.
Bear in mind when choosing security that the higher-security algorithms need higher processing power to encrypt and hash, and that hackers would need a farm of supercomputers to crack encrypted data. There may be no need to select the very strongest algorithms.
To increase the security on newer Drayteks, just select the ‘Medium’ security method which disables the less secure algorithms. (Note that the less secure algorithms DES, 3DES, MD5, G1 and G2 are enabled when ‘Basic’ is selected.)
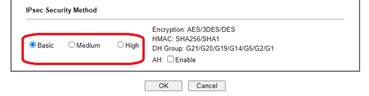
On older Drayteks, the procedure is different. Just disable AH, DES and 3DES (this will suffice for Windows, as we will see in a moment)
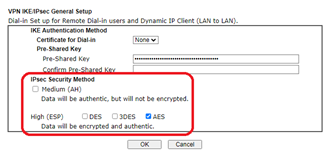
Windows is preconfigured with the following proposals:
- AES256/SHA1/G20
- AES128/SHA1/G19
- AES256/SHA1/G14
- 3DES/SHA1/G14
- 3DES/SHA1/G2
So, by removing DES and 3DES from the router, Windows will not be able to use MD5, G1 or G2.
Now, this is a brief overview of IPsec. It is not the full story – there are actually two phases of security negotiations in the first version of IPsec (IKEv1) and different proposals could be used in each. Lets not go there now. Suffice to say that the Draytek makes it easy for us. And the latest version of IPsec, IKEv2, makes all this a whole lot simpler.